Table of Contents
This post will talk about using mobile cell phones and cellular networks for security, privacy & anonymity and why that can’t really happen. It is unfortunate that serious privacy and anonymity with modern smartphones using one of the popular operating systems on a mobile network is pretty much unattainable. The problem is everyone wants to use a modern non-privacy-focused smartphone and a popular operating system, plus we connect to insecure mobile networks that track everything we do; it’s a problem. If you were to design a solution for de-anonymizing you and eroding your privacy, a mobile phone and network would be the solution that you would come up with. It is perfect for it – even if you’re using a proxy.
So it’s really an uphill battle to get security privacy and anonymity with your modern mobile cell phone and mobile companies. So for me with mobile devices and phones, it’s more of a best-effort approach to privacy and anonymity so, for example, I’m going to use a secure messaging app like signal but I acknowledge that if I’m using an iPhone, Apple, my network provider, can control my phone if they really want to and that’s the same for all other major operating systems and networks like Android, Windows, BlackBerry et cetera.
we simply have less control over these devices than we do over desktops and laptops. Replacing the operating system on these phones is deliberately made difficult and it is much harder to investigate malware and find and remove potential undesirable programs on these smartphones. But let me clarify, what I mean is you’re still pretty safe using a mobile banking app on an iPhone as long as the app and infrastructure are securely designed however if you want serious privacy and anonymity from a serious adversary who is well resourced like a nation-state is near impossible. Well-designed security applications like mobile banking apps are helping to mitigate some of the underlying problems of the mobile network and the mobile platform. So I’ll just summarize the issues of why serious privacy and anonymity is a lost cause and why you should consider its best efforts really, phone and cellular network security could be a cost to itself really. And later on, I’m going to provide some mitigations to these issues that we go through.
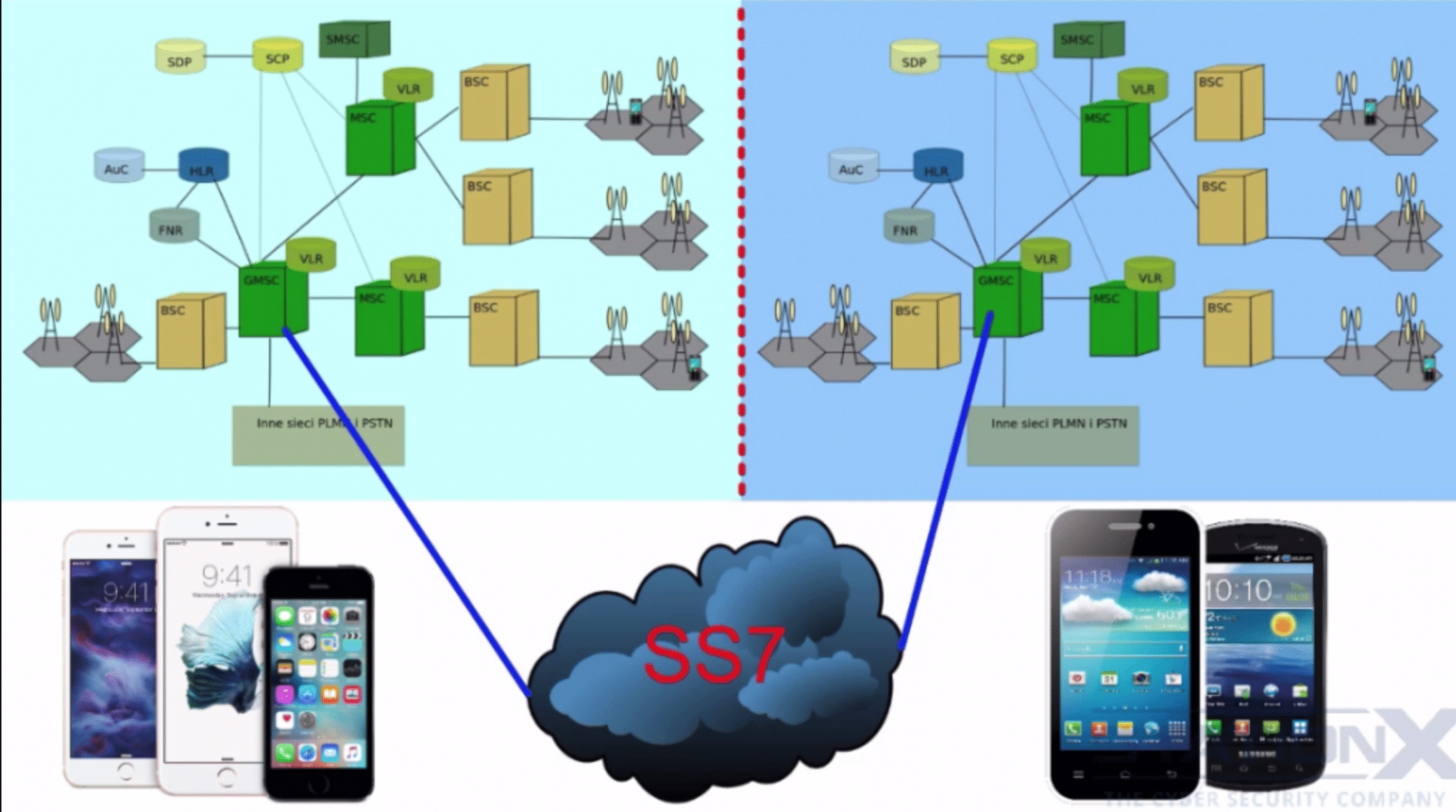
In the image above you can see two mobile operators connected by the SS7 protocol. So let’s consider the issues with the network provider or operator issues when it comes to privacy and anonymity and seFirstll firs,t of all, they can record your voice cand they do if they need to, they can record and log the content of your internet data traffic anything unencrypted. That would be anything that is encrypted they would have to do an active attack which will be more difficult which is why end-to-end encryption is always what you need. The operator can read and store SMS messages, MMS messages, and they can send a short message type zero also known as a silent SMS which can be sent to keep track of you by your geographic location data. Some of them provide software updates that can manipulate your phone which means they can essentially take control of your phone but this will depend on your phone and your provider as some countries and networks are very different when it comes to software updates.
They can also do what’s called Tower dorms of all the connected phones over a given time on request. This is to help track and cross-correlate who you know and who might be in the area at the same time, this is done for third parties on request. When you are connected to their, network, they can know your MAC, address which is unique to your phone, and if you purchased it, then it uniquely identifies you.
They record metadata like call duration, course location, callers and receivers of calls, time of calls, time of SMS and picture messages, Internet usage. And then over the air, an advisory can possibly get your subscriber identity your IMZI and with IMZI attached they can get the TMSI with TMSI call patterns
Over the air, an adversary can potentially get a hold of your precise location through location-based services and triangulation in built-up areas with more towers. A more precise location can be made fewer towers in a less built-up area variation is less precise. Providers between each other can also exchange data about the location of devices for more accuracy in locating.
Your data, voice, SMS can be intercepted by adversaries with the right equipment if there is no encryption or there is weak encryption. The encryption will depend on the provider that you have chosen and the network implementation and some governments have pressured providers to deliberately weaken encryption for that purpose.
So those are the general concerns that you would have in terms of privacy and anonymity when it comes to your provider and the general over-the-air issues.
FAQs
1. How do smartphones invade privacy?
Smartphones can invade privacy in a number of ways. For example, many smartphones are equipped with GPS tracking that can pinpoint a user's location at any given time. This can be used by companies to track consumer behavior, or by law enforcement to track criminal activity. Additionally, many smartphones are equipped with cameras and microphones that can be used to record and store personal conversations and images without the user's knowledge or consent. This can be especially harmful if the recordings include sensitive personal information or images.
2. Do you think mobile phone tracking is a violation of a person’s privacy?
I believe that mobile phone tracking is a violation of a person's privacy. I feel like it invades my personal space and makes me uncomfortable. I would never want someone to know where I am at any given time without my consent because it can be used in many ways. For example, if you're being stalked or harassed by people that don't like you, they could track your location, which could put you in danger.
3. Why is mobile privacy important?
Mobile privacy is important because it keeps your personal information safe and secure. People use their mobile devices for a variety of activities, from banking and shopping to social networking and communicating. All of this personal data can be accessed and used by third-party companies if the user's privacy isn't protected.
4. Can your phone hear your conversations?
There is no evidence that your phone can hear your conversations. However, there are a few things you can do to protect your privacy. First, use a passcode to lock your phone. This will make it more difficult for someone to access your information if they get their hands on your phone. Second, delete any conversations that you don't want others to hear. This will help protect your privacy and keep your conversations confidential.
5 Are smartphones a threat to privacy?
According to some experts, smartphones are a threat to privacy because they can easily be converted into surveillance devices without impairing their functionality. Additionally, they assert that private hackers, the government, or cloud service providers can use smartphones as tracking devices.


